Nearly 600,000 Records Exposed Online in Leading EV-Service Provider Data Breach
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to WebsitePlanet about a non-password-protected database that contained 573,309 records, which included invoices and customer information from an American-based EV-services provider.
The rise of electric vehicles (EVs) has created a shift in the automotive industry, driven by increasing environmental awareness, government incentives, and advancements in battery technology. EV adoption has grown significantly as more automakers introduce electric models, offering consumers a cleaner and more sustainable alternative to traditional vehicles. With the surge in electric vehicles, the most significant challenge is the need to build a charging infrastructure. According to data as of 2023, it is estimated that there are 2,442,270 electric vehicles registered in the United States and 132,783 in Canada. Consumers often face concerns about the availability, accessibility, and speed of public charging stations. This growth has created a big demand in installing home charging networks. In today’s connected world, even offline services selling physical products can lead to an online data exposure.
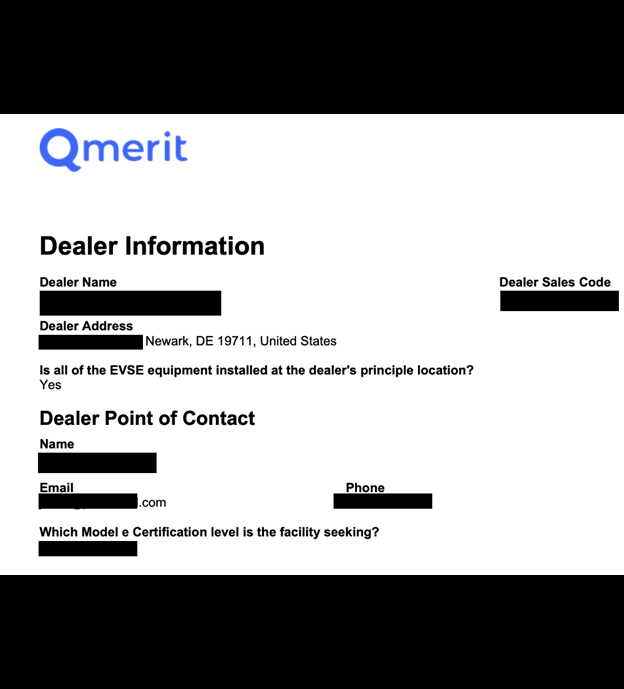
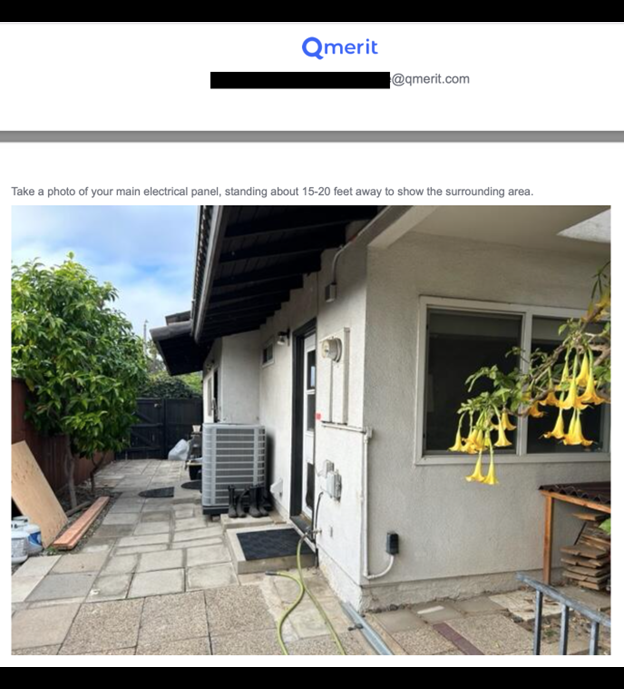
The publicly exposed database contained 573,309 documents with a total size of 585.81 GB. These files included work invoices, price proposals, electrical permits, and surveys with information submitted by customers, including pictures of their homes and charger location details. Upon further review, I identified the data belonged to Texas-based Qmerit, a company that provides a suite of EV-related services such as installation and maintenance of EV charging infrastructure for residential, commercial, and fleet applications. I immediately sent them a responsible disclosure notice of my discovery, and access to the documents was restricted shortly after. I received the following reply: “Thank you for alerting us to this issue. We take security issues and the protection of PII very seriously and are taking immediate technical steps to investigate the situation”. It is unclear how long the records were exposed or if anyone else may have had access to them. Only an internal forensic audit could identify any additional access to the exposed documents. Qmerit acted fast and professionally to secure the data immediately after my notification.
According to their website: Qmerit is North America’s leading provider of distributed workforce management for EV charging and other energy transition technologies, simplifying electrification adoption for residential, commercial, and industrial markets.
In a 2024 press release, Qmerit announced that the company was selected as a preferred installer for GM Energy’s residential products and has partnered with top automakers from the U.S., Europe, and Asia. Qmerit claims to have completed over 269,000 home and business EV charger installations throughout North America.
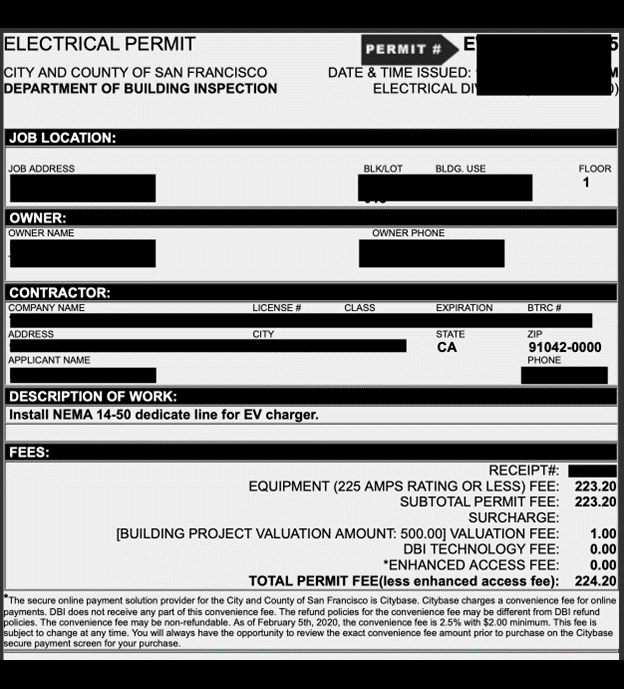
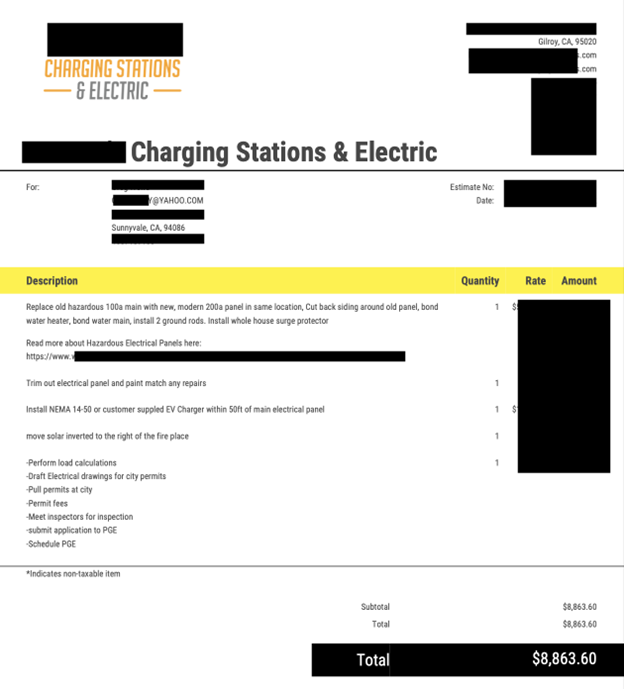
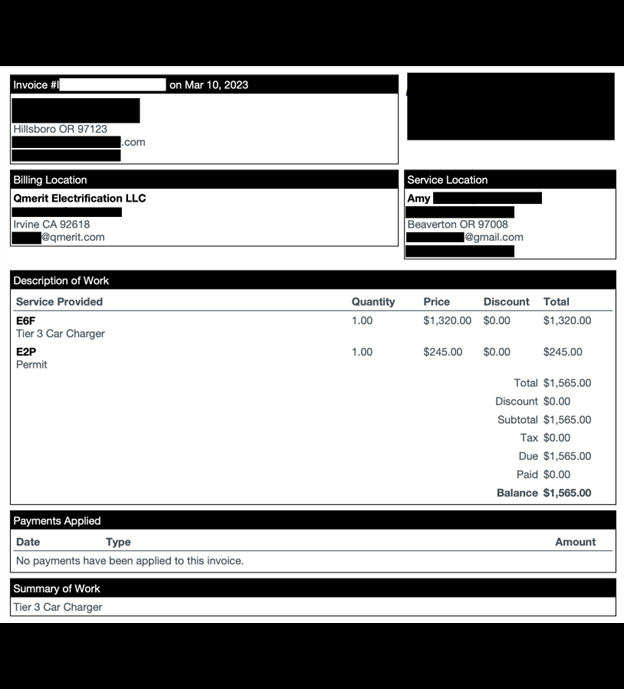
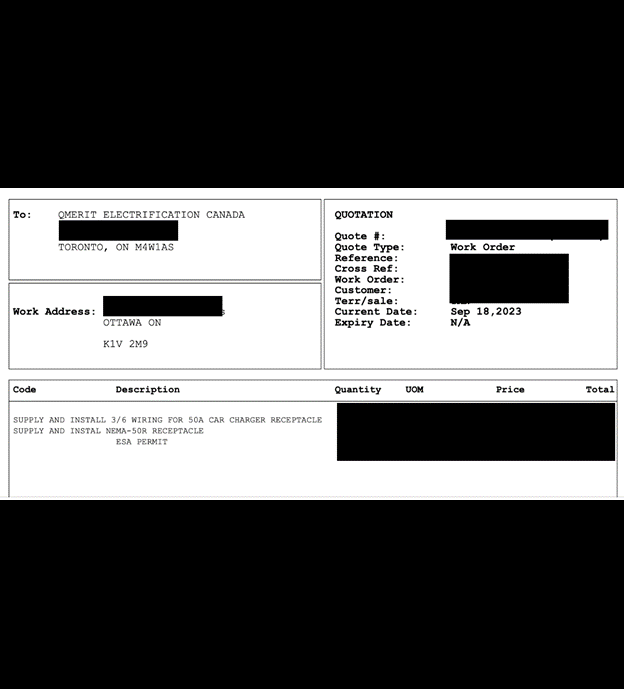
Here are several examples of the types of documents contained in the database.
The applications also included customer names, customer home addresses, and other specific property details, which necessitates careful handling to protect customer privacy. Improper management or exposure of this sensitive information could heighten the risk of unauthorized access to these properties, presenting a tangible security concern for homeowners.
Any data breach that exposes customer or contractor invoices can pose numerous potential risks. Fraud is a significant concern when invoices are involved. According to a 2023 survey of 2,750 businesses, there were an estimated 34,000 cases of invoice fraud resulting in an approximate average annual cost of $280,000 per business. It is important to clarify that I am not stating nor implying that Qmerit’s customers or contractors are specifically at risk of invoice fraud, I am only saying that it is recognized as a prevalent issue across various industries. Understanding the potential risks can help companies prepare and implement strategies to mitigate damage or even prevent invoice fraud.
Exposed personal information such as names, addresses, phone numbers, and emails can be used for attempts at identity theft or more complex forms of fraud. Cybercriminals could potentially impersonate customers, contractors, or Qmerit representatives and use insider information for fraudulent activities that target contractors and customers alike. According to the FBI, social engineering accounts for 98% of all cyberattacks. Attackers could potentially use the leaked information to conduct targeted phishing campaigns; they could reference the details from the invoices to deceive customers into sharing more sensitive information. This could be offline (in the form of a phone call) or online through email communications.
Additionally, the exposed documents that contain details and images of the interior or exterior of homes could pose privacy concerns for customers. They could also be used to identify properties that are potentially vulnerable to physical theft. Criminals armed with names of customers and installers, dates of completed or proposed work, quotation details, permit information, and other specifics would have a wealth of insider knowledge that could be used to build trust and facilitate a successful social engineering attack. Once again, I am only providing a hypothetical scenario to illustrate how criminals could potentially use exposed data for malicious purposes, without implying any current risk associated with specific practices or entities.
I highly recommend that customers and contractors always validate any suspicious requests for additional information, be it credit card or payment details, or sensitive personal information such as their SSN or tax ID numbers. Use only official communication channels from the company and always make sure you know to whom you are providing your personal information. For companies that collect and store customer information and invoices, I recommend that they encrypt sensitive data, conduct regular security audits, and stay up to date with the most current data-protection practices. This includes access control and giving documents a limited lifespan or expiration date. Ensuring that records containing PII are not stored after they are no longer used is a simple way to prevent future data exposures.
I imply no wrongdoing by Qmerit or their contractors. I am also not implying that customer or contractor data was ever at risk or that these individuals are in imminent danger of being targeted by criminals. It is unknown how long the records were exposed or if anyone else may have had access to the publicly exposed database.
As an ethical security researcher, I never download the data I discover and only review a limited number of documents for validation and reporting purposes. I publish my findings so that more people can be aware of the risks and avoid falling prey to criminal ploys. I also provide real-world and hypothetical examples of how exposed records could lead to potential privacy risks to promote best practices for cybersecurity and data protection.