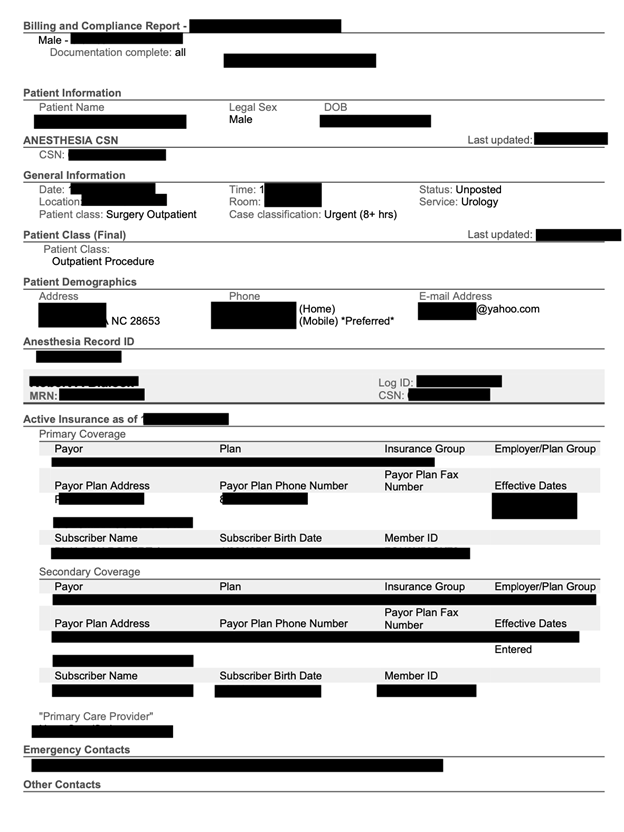
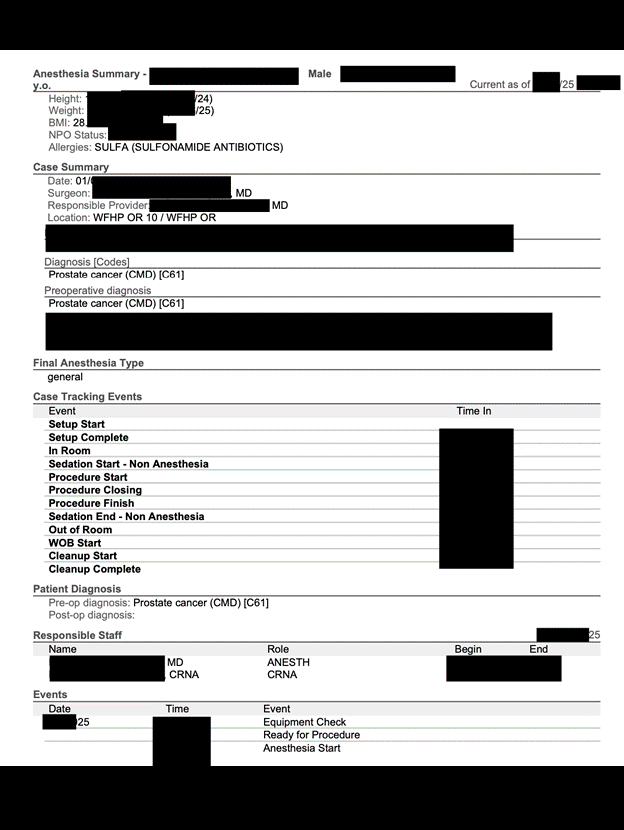
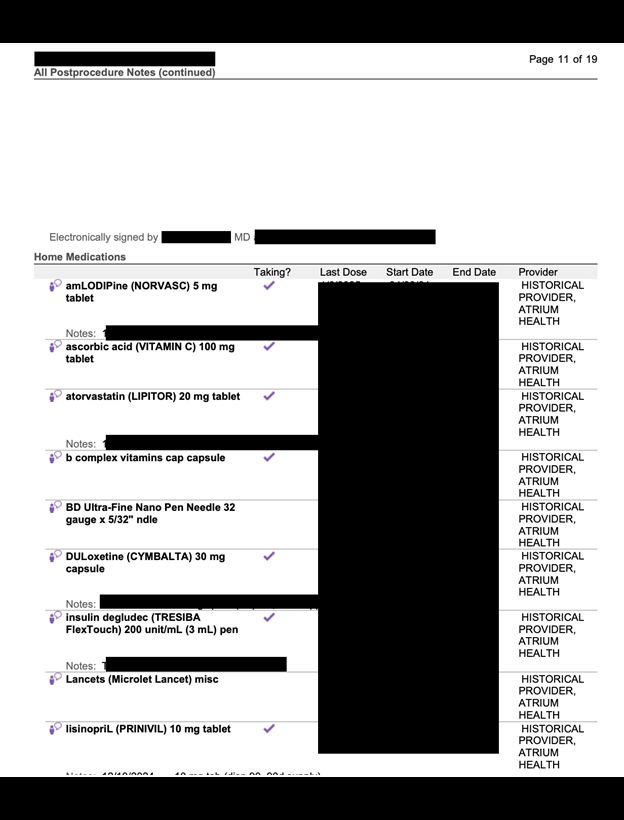
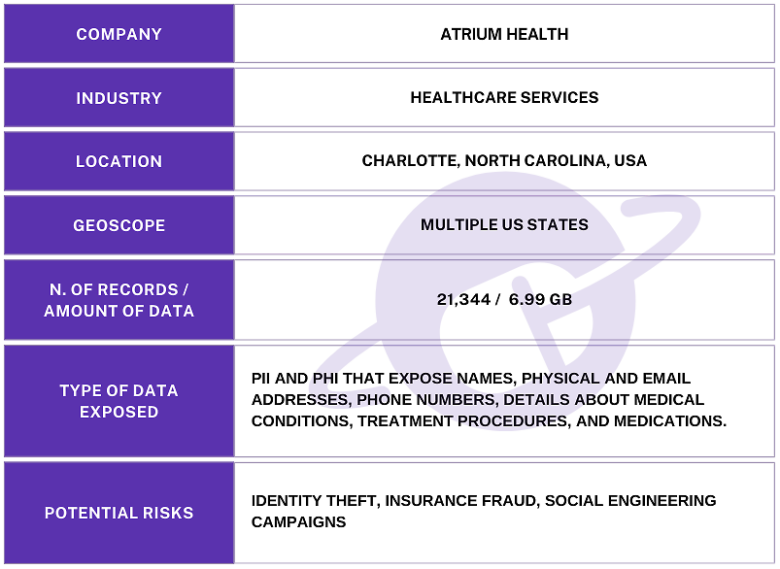
 The publicly exposed database was not password-protected nor encrypted. It contained 21,344 records with a total size of 6.99 GB. The name of the database indicated that it was an FTP storage repository. In a limited sampling of the exposed documents, I saw .PDF files marked as Billing and Compliance Reports. These contained a detailed account of patient data, such as: Patient PII, insurance coverage details, emergency contacts, anesthesia summary, case summary, diagnosis, case tracking details, names of medical staff, medications administered, patient vital statistics, family medical history, patient medical history, additional notes and summaries by doctors or medical staff.
The PDF documents’ metadata indicated that these were “Software Billing and Compliance Reports” belonging to a medical software company, and contained a detailed analysis and key metrics related to medical billing and healthcare services provided. I immediately contacted that company and provided the details of my discovery. They indicated that they did not own or manage the database and that it was a customer using their electronic health record (EHR) system. Based on the information I provided, this medical software company was able to identify who the documents belonged to and notify that organization. Public access was restricted the same day.
They did not disclose to me who the documents belonged to. However, upon further research, I found a folder marked “Production/Atrium Reports” in the database. The records inside it contained names of medical staff that all appeared to be affiliated with Atrium Health, based on publicly available information .
According to a press release, Advocate Aurora Health and Atrium Health merged in 2022 to create Advocate Health — the third-largest nonprofit, integrated healthcare system in the United States. With its headquarters in Charlotte, North Carolina, the system extends its services across six states: Illinois, Wisconsin, North Carolina, South Carolina, Georgia, and Alabama. The Advocate Health network includes 67 hospitals and more than 500 care locations, and a workforce of an estimated 155,000 professionals, including 10,000 physicians.
I reached out to Atrium Health to inform them that I am an ethical cybersecurity researcher and thus I did not download any sensitive health data, I have no ill intent, and my primary motive is data protection. I received a reply from their cyber incident response team stating: “Thank you for bringing this matter to our attention. We immediately launched an investigation to ensure the issue is resolved. – Advocate Health Cyber Security Team”
It is not known if the database was owned and managed by Atrium Health directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
As a security researcher, the fact that the hospital network has an incident response team and acted quickly to resolve the issue is a good sign and shows a commitment to data security. Furthermore, it should be noted that the medical software company I initially contacted was not involved with the exposure and was very helpful in contributing to secure the publicly accessible records.
Medical compliance documents outline the policies, procedures, and regulations that healthcare providers and organizations must follow to ensure ethical and legal medical billing and coding practices. These documents provide clear billing details, reducing administrative inefficiencies caused by billing or coding errors and providing transparency and accountability. As the documents include personally identifiable health information, they could potentially be subject to regulations such as HIPAA, which mandates stringent security measures.
In this case, each file was labeled as “Billing and Compliance Report” and contained sections that included patient information, anesthesia CSN number, patient class, demographics, anesthesia record ID, active insurance, emergency contact details, case summary, procedure, diagnosis, case tracking events, medications administered, attestation information, vitals, family history, substance use history, post procedure notes, procedure summary, follow up notes, operative notes, and plan of care.
Any data exposure of detailed medical records could potentially pose significant risks. The PII and PHI contained in these records could potentially lead to identity theft, insurance fraud, or social engineering campaigns to obtain additional personal or financial information. Unauthorized access to a patient’s medical history could provide cybercriminals with enough information to attempt a wide range of fraudulent activities. There is no indication that any of Atrium Health’s patient information or health records were at risk of these types of scenarios. The intention is solely to illustrate real-world potential threats based on past cybersecurity incidents within the healthcare sector.
Patient data — such as confidential medical histories, diagnoses, medications, and family health data — is highly valuable on the dark web, making it a prime target for cybercriminals and even nation state actors. Several reports have estimated that a single health record can sell for up to $1,000; for comparison, credit card details sell for about $5, while Social Security numbers are valued at just $1 on the dark web. It is estimated that 97% of threat actors were financially motivated to commit their crimes, so it comes as no surprise that medical providers are one of the biggest targets for cybercriminals.
As such, hospitals and medical providers must take additional security steps to protect their operational data as well as the cloud storage databases where sensitive patient information is stored. One of the easiest ways to do this would be to use strong encryption protocols for both stored and transmitted data. Using encryption can help ensure that patient information remains inaccessible and unreadable even if exposed in a data breach.
In this specific instance, all of the records I saw were in PDF format, readable, and publicly accessible. However, PDF files can easily be password protected, which provides an additional layer of defense in the event of a data exposure. I would also recommend that multi-factor authentication (MFA) be required for all users who have access to cloud storage repositories. MFA, when configured properly, is a great first line of defense for preventing unauthorized login attempts and access. Another good idea is to create role-based access controls (RBAC), limiting access to potentially sensitive records to authorized personnel only.
As a general rule that applies to any industry or service that collects and stores potentially sensitive information, routine security audits and vulnerability assessments should be conducted regularly to identify and patch weaknesses in their systems. I also recommend implementing active monitoring and network detection systems that can help identify unusual or suspicious activity. Real-time monitoring of systems and networks can help identify and respond to potential security incidents before they cause significant harm. Anyone with network access should receive ongoing cybersecurity training to recognize phishing attempts and other social engineering threats.
In December 2024 Atrium Health disclosed a privacy breach impacting nearly 600,000 patients due to online tracking tools embedded in its patient portal from January 2015 to July 2019. These tools, which included tracking pixels from third-party companies like Meta and Google, may have collected and transmitted patient data — such as IP addresses, browsing activity, and personal details from online forms — without consent. Although Atrium Health could not determine if sensitive information was misused, they are treating all affected patients as potentially impacted. According to the report, this was the second data incident the organization reported in 2024, following a phishing attack that exposed information of around 32,000 patients. These incidents underscore ongoing concerns about digital tracking in healthcare, HIPAA compliance, and malicious attempts to access hospital data.
I imply no wrongdoing by Atrium Health, its employees, any contractors and/or its affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a judgement or reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, manipulate, or alter any data I discover. I only take a limited number of screenshots solely for verification purposes and redact those images to protect any potentially sensitive information. I do not conduct any activities beyond identifying potential security vulnerabilities and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected nor encrypted. It contained 21,344 records with a total size of 6.99 GB. The name of the database indicated that it was an FTP storage repository. In a limited sampling of the exposed documents, I saw .PDF files marked as Billing and Compliance Reports. These contained a detailed account of patient data, such as: Patient PII, insurance coverage details, emergency contacts, anesthesia summary, case summary, diagnosis, case tracking details, names of medical staff, medications administered, patient vital statistics, family medical history, patient medical history, additional notes and summaries by doctors or medical staff.
The PDF documents’ metadata indicated that these were “Software Billing and Compliance Reports” belonging to a medical software company, and contained a detailed analysis and key metrics related to medical billing and healthcare services provided. I immediately contacted that company and provided the details of my discovery. They indicated that they did not own or manage the database and that it was a customer using their electronic health record (EHR) system. Based on the information I provided, this medical software company was able to identify who the documents belonged to and notify that organization. Public access was restricted the same day.
They did not disclose to me who the documents belonged to. However, upon further research, I found a folder marked “Production/Atrium Reports” in the database. The records inside it contained names of medical staff that all appeared to be affiliated with Atrium Health, based on publicly available information .
According to a press release, Advocate Aurora Health and Atrium Health merged in 2022 to create Advocate Health — the third-largest nonprofit, integrated healthcare system in the United States. With its headquarters in Charlotte, North Carolina, the system extends its services across six states: Illinois, Wisconsin, North Carolina, South Carolina, Georgia, and Alabama. The Advocate Health network includes 67 hospitals and more than 500 care locations, and a workforce of an estimated 155,000 professionals, including 10,000 physicians.
I reached out to Atrium Health to inform them that I am an ethical cybersecurity researcher and thus I did not download any sensitive health data, I have no ill intent, and my primary motive is data protection. I received a reply from their cyber incident response team stating: “Thank you for bringing this matter to our attention. We immediately launched an investigation to ensure the issue is resolved. – Advocate Health Cyber Security Team”
It is not known if the database was owned and managed by Atrium Health directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
As a security researcher, the fact that the hospital network has an incident response team and acted quickly to resolve the issue is a good sign and shows a commitment to data security. Furthermore, it should be noted that the medical software company I initially contacted was not involved with the exposure and was very helpful in contributing to secure the publicly accessible records.
Medical compliance documents outline the policies, procedures, and regulations that healthcare providers and organizations must follow to ensure ethical and legal medical billing and coding practices. These documents provide clear billing details, reducing administrative inefficiencies caused by billing or coding errors and providing transparency and accountability. As the documents include personally identifiable health information, they could potentially be subject to regulations such as HIPAA, which mandates stringent security measures.
In this case, each file was labeled as “Billing and Compliance Report” and contained sections that included patient information, anesthesia CSN number, patient class, demographics, anesthesia record ID, active insurance, emergency contact details, case summary, procedure, diagnosis, case tracking events, medications administered, attestation information, vitals, family history, substance use history, post procedure notes, procedure summary, follow up notes, operative notes, and plan of care.
Any data exposure of detailed medical records could potentially pose significant risks. The PII and PHI contained in these records could potentially lead to identity theft, insurance fraud, or social engineering campaigns to obtain additional personal or financial information. Unauthorized access to a patient’s medical history could provide cybercriminals with enough information to attempt a wide range of fraudulent activities. There is no indication that any of Atrium Health’s patient information or health records were at risk of these types of scenarios. The intention is solely to illustrate real-world potential threats based on past cybersecurity incidents within the healthcare sector.
Patient data — such as confidential medical histories, diagnoses, medications, and family health data — is highly valuable on the dark web, making it a prime target for cybercriminals and even nation state actors. Several reports have estimated that a single health record can sell for up to $1,000; for comparison, credit card details sell for about $5, while Social Security numbers are valued at just $1 on the dark web. It is estimated that 97% of threat actors were financially motivated to commit their crimes, so it comes as no surprise that medical providers are one of the biggest targets for cybercriminals.
As such, hospitals and medical providers must take additional security steps to protect their operational data as well as the cloud storage databases where sensitive patient information is stored. One of the easiest ways to do this would be to use strong encryption protocols for both stored and transmitted data. Using encryption can help ensure that patient information remains inaccessible and unreadable even if exposed in a data breach.
In this specific instance, all of the records I saw were in PDF format, readable, and publicly accessible. However, PDF files can easily be password protected, which provides an additional layer of defense in the event of a data exposure. I would also recommend that multi-factor authentication (MFA) be required for all users who have access to cloud storage repositories. MFA, when configured properly, is a great first line of defense for preventing unauthorized login attempts and access. Another good idea is to create role-based access controls (RBAC), limiting access to potentially sensitive records to authorized personnel only.
As a general rule that applies to any industry or service that collects and stores potentially sensitive information, routine security audits and vulnerability assessments should be conducted regularly to identify and patch weaknesses in their systems. I also recommend implementing active monitoring and network detection systems that can help identify unusual or suspicious activity. Real-time monitoring of systems and networks can help identify and respond to potential security incidents before they cause significant harm. Anyone with network access should receive ongoing cybersecurity training to recognize phishing attempts and other social engineering threats.
In December 2024 Atrium Health disclosed a privacy breach impacting nearly 600,000 patients due to online tracking tools embedded in its patient portal from January 2015 to July 2019. These tools, which included tracking pixels from third-party companies like Meta and Google, may have collected and transmitted patient data — such as IP addresses, browsing activity, and personal details from online forms — without consent. Although Atrium Health could not determine if sensitive information was misused, they are treating all affected patients as potentially impacted. According to the report, this was the second data incident the organization reported in 2024, following a phishing attack that exposed information of around 32,000 patients. These incidents underscore ongoing concerns about digital tracking in healthcare, HIPAA compliance, and malicious attempts to access hospital data.
I imply no wrongdoing by Atrium Health, its employees, any contractors and/or its affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a judgement or reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, manipulate, or alter any data I discover. I only take a limited number of screenshots solely for verification purposes and redact those images to protect any potentially sensitive information. I do not conduct any activities beyond identifying potential security vulnerabilities and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.

Over 20 Thousand Medical Records With PII and Patient Info Exposed in Health Data Breach
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to Website Planet about a non-password-protected database that contained 21,344 records belonging to Atrium Health — a Charlotte, North Carolina-based network of hospitals, clinics, and specialty centers across the Southeast.
![WSP-Atrium-data-breach-key-elements]() The publicly exposed database was not password-protected nor encrypted. It contained 21,344 records with a total size of 6.99 GB. The name of the database indicated that it was an FTP storage repository. In a limited sampling of the exposed documents, I saw .PDF files marked as Billing and Compliance Reports. These contained a detailed account of patient data, such as: Patient PII, insurance coverage details, emergency contacts, anesthesia summary, case summary, diagnosis, case tracking details, names of medical staff, medications administered, patient vital statistics, family medical history, patient medical history, additional notes and summaries by doctors or medical staff.
The PDF documents’ metadata indicated that these were “Software Billing and Compliance Reports” belonging to a medical software company, and contained a detailed analysis and key metrics related to medical billing and healthcare services provided. I immediately contacted that company and provided the details of my discovery. They indicated that they did not own or manage the database and that it was a customer using their electronic health record (EHR) system. Based on the information I provided, this medical software company was able to identify who the documents belonged to and notify that organization. Public access was restricted the same day.
They did not disclose to me who the documents belonged to. However, upon further research, I found a folder marked “Production/Atrium Reports” in the database. The records inside it contained names of medical staff that all appeared to be affiliated with Atrium Health, based on publicly available information .
According to a press release, Advocate Aurora Health and Atrium Health merged in 2022 to create Advocate Health — the third-largest nonprofit, integrated healthcare system in the United States. With its headquarters in Charlotte, North Carolina, the system extends its services across six states: Illinois, Wisconsin, North Carolina, South Carolina, Georgia, and Alabama. The Advocate Health network includes 67 hospitals and more than 500 care locations, and a workforce of an estimated 155,000 professionals, including 10,000 physicians.
I reached out to Atrium Health to inform them that I am an ethical cybersecurity researcher and thus I did not download any sensitive health data, I have no ill intent, and my primary motive is data protection. I received a reply from their cyber incident response team stating: “Thank you for bringing this matter to our attention. We immediately launched an investigation to ensure the issue is resolved. – Advocate Health Cyber Security Team”
It is not known if the database was owned and managed by Atrium Health directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
As a security researcher, the fact that the hospital network has an incident response team and acted quickly to resolve the issue is a good sign and shows a commitment to data security. Furthermore, it should be noted that the medical software company I initially contacted was not involved with the exposure and was very helpful in contributing to secure the publicly accessible records.
Medical compliance documents outline the policies, procedures, and regulations that healthcare providers and organizations must follow to ensure ethical and legal medical billing and coding practices. These documents provide clear billing details, reducing administrative inefficiencies caused by billing or coding errors and providing transparency and accountability. As the documents include personally identifiable health information, they could potentially be subject to regulations such as HIPAA, which mandates stringent security measures.
In this case, each file was labeled as “Billing and Compliance Report” and contained sections that included patient information, anesthesia CSN number, patient class, demographics, anesthesia record ID, active insurance, emergency contact details, case summary, procedure, diagnosis, case tracking events, medications administered, attestation information, vitals, family history, substance use history, post procedure notes, procedure summary, follow up notes, operative notes, and plan of care.
Any data exposure of detailed medical records could potentially pose significant risks. The PII and PHI contained in these records could potentially lead to identity theft, insurance fraud, or social engineering campaigns to obtain additional personal or financial information. Unauthorized access to a patient’s medical history could provide cybercriminals with enough information to attempt a wide range of fraudulent activities. There is no indication that any of Atrium Health’s patient information or health records were at risk of these types of scenarios. The intention is solely to illustrate real-world potential threats based on past cybersecurity incidents within the healthcare sector.
Patient data — such as confidential medical histories, diagnoses, medications, and family health data — is highly valuable on the dark web, making it a prime target for cybercriminals and even nation state actors. Several reports have estimated that a single health record can sell for up to $1,000; for comparison, credit card details sell for about $5, while Social Security numbers are valued at just $1 on the dark web. It is estimated that 97% of threat actors were financially motivated to commit their crimes, so it comes as no surprise that medical providers are one of the biggest targets for cybercriminals.
As such, hospitals and medical providers must take additional security steps to protect their operational data as well as the cloud storage databases where sensitive patient information is stored. One of the easiest ways to do this would be to use strong encryption protocols for both stored and transmitted data. Using encryption can help ensure that patient information remains inaccessible and unreadable even if exposed in a data breach.
In this specific instance, all of the records I saw were in PDF format, readable, and publicly accessible. However, PDF files can easily be password protected, which provides an additional layer of defense in the event of a data exposure. I would also recommend that multi-factor authentication (MFA) be required for all users who have access to cloud storage repositories. MFA, when configured properly, is a great first line of defense for preventing unauthorized login attempts and access. Another good idea is to create role-based access controls (RBAC), limiting access to potentially sensitive records to authorized personnel only.
As a general rule that applies to any industry or service that collects and stores potentially sensitive information, routine security audits and vulnerability assessments should be conducted regularly to identify and patch weaknesses in their systems. I also recommend implementing active monitoring and network detection systems that can help identify unusual or suspicious activity. Real-time monitoring of systems and networks can help identify and respond to potential security incidents before they cause significant harm. Anyone with network access should receive ongoing cybersecurity training to recognize phishing attempts and other social engineering threats.
In December 2024 Atrium Health disclosed a privacy breach impacting nearly 600,000 patients due to online tracking tools embedded in its patient portal from January 2015 to July 2019. These tools, which included tracking pixels from third-party companies like Meta and Google, may have collected and transmitted patient data — such as IP addresses, browsing activity, and personal details from online forms — without consent. Although Atrium Health could not determine if sensitive information was misused, they are treating all affected patients as potentially impacted. According to the report, this was the second data incident the organization reported in 2024, following a phishing attack that exposed information of around 32,000 patients. These incidents underscore ongoing concerns about digital tracking in healthcare, HIPAA compliance, and malicious attempts to access hospital data.
I imply no wrongdoing by Atrium Health, its employees, any contractors and/or its affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a judgement or reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, manipulate, or alter any data I discover. I only take a limited number of screenshots solely for verification purposes and redact those images to protect any potentially sensitive information. I do not conduct any activities beyond identifying potential security vulnerabilities and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected nor encrypted. It contained 21,344 records with a total size of 6.99 GB. The name of the database indicated that it was an FTP storage repository. In a limited sampling of the exposed documents, I saw .PDF files marked as Billing and Compliance Reports. These contained a detailed account of patient data, such as: Patient PII, insurance coverage details, emergency contacts, anesthesia summary, case summary, diagnosis, case tracking details, names of medical staff, medications administered, patient vital statistics, family medical history, patient medical history, additional notes and summaries by doctors or medical staff.
The PDF documents’ metadata indicated that these were “Software Billing and Compliance Reports” belonging to a medical software company, and contained a detailed analysis and key metrics related to medical billing and healthcare services provided. I immediately contacted that company and provided the details of my discovery. They indicated that they did not own or manage the database and that it was a customer using their electronic health record (EHR) system. Based on the information I provided, this medical software company was able to identify who the documents belonged to and notify that organization. Public access was restricted the same day.
They did not disclose to me who the documents belonged to. However, upon further research, I found a folder marked “Production/Atrium Reports” in the database. The records inside it contained names of medical staff that all appeared to be affiliated with Atrium Health, based on publicly available information .
According to a press release, Advocate Aurora Health and Atrium Health merged in 2022 to create Advocate Health — the third-largest nonprofit, integrated healthcare system in the United States. With its headquarters in Charlotte, North Carolina, the system extends its services across six states: Illinois, Wisconsin, North Carolina, South Carolina, Georgia, and Alabama. The Advocate Health network includes 67 hospitals and more than 500 care locations, and a workforce of an estimated 155,000 professionals, including 10,000 physicians.
I reached out to Atrium Health to inform them that I am an ethical cybersecurity researcher and thus I did not download any sensitive health data, I have no ill intent, and my primary motive is data protection. I received a reply from their cyber incident response team stating: “Thank you for bringing this matter to our attention. We immediately launched an investigation to ensure the issue is resolved. – Advocate Health Cyber Security Team”
It is not known if the database was owned and managed by Atrium Health directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
As a security researcher, the fact that the hospital network has an incident response team and acted quickly to resolve the issue is a good sign and shows a commitment to data security. Furthermore, it should be noted that the medical software company I initially contacted was not involved with the exposure and was very helpful in contributing to secure the publicly accessible records.
Medical compliance documents outline the policies, procedures, and regulations that healthcare providers and organizations must follow to ensure ethical and legal medical billing and coding practices. These documents provide clear billing details, reducing administrative inefficiencies caused by billing or coding errors and providing transparency and accountability. As the documents include personally identifiable health information, they could potentially be subject to regulations such as HIPAA, which mandates stringent security measures.
In this case, each file was labeled as “Billing and Compliance Report” and contained sections that included patient information, anesthesia CSN number, patient class, demographics, anesthesia record ID, active insurance, emergency contact details, case summary, procedure, diagnosis, case tracking events, medications administered, attestation information, vitals, family history, substance use history, post procedure notes, procedure summary, follow up notes, operative notes, and plan of care.
Any data exposure of detailed medical records could potentially pose significant risks. The PII and PHI contained in these records could potentially lead to identity theft, insurance fraud, or social engineering campaigns to obtain additional personal or financial information. Unauthorized access to a patient’s medical history could provide cybercriminals with enough information to attempt a wide range of fraudulent activities. There is no indication that any of Atrium Health’s patient information or health records were at risk of these types of scenarios. The intention is solely to illustrate real-world potential threats based on past cybersecurity incidents within the healthcare sector.
Patient data — such as confidential medical histories, diagnoses, medications, and family health data — is highly valuable on the dark web, making it a prime target for cybercriminals and even nation state actors. Several reports have estimated that a single health record can sell for up to $1,000; for comparison, credit card details sell for about $5, while Social Security numbers are valued at just $1 on the dark web. It is estimated that 97% of threat actors were financially motivated to commit their crimes, so it comes as no surprise that medical providers are one of the biggest targets for cybercriminals.
As such, hospitals and medical providers must take additional security steps to protect their operational data as well as the cloud storage databases where sensitive patient information is stored. One of the easiest ways to do this would be to use strong encryption protocols for both stored and transmitted data. Using encryption can help ensure that patient information remains inaccessible and unreadable even if exposed in a data breach.
In this specific instance, all of the records I saw were in PDF format, readable, and publicly accessible. However, PDF files can easily be password protected, which provides an additional layer of defense in the event of a data exposure. I would also recommend that multi-factor authentication (MFA) be required for all users who have access to cloud storage repositories. MFA, when configured properly, is a great first line of defense for preventing unauthorized login attempts and access. Another good idea is to create role-based access controls (RBAC), limiting access to potentially sensitive records to authorized personnel only.
As a general rule that applies to any industry or service that collects and stores potentially sensitive information, routine security audits and vulnerability assessments should be conducted regularly to identify and patch weaknesses in their systems. I also recommend implementing active monitoring and network detection systems that can help identify unusual or suspicious activity. Real-time monitoring of systems and networks can help identify and respond to potential security incidents before they cause significant harm. Anyone with network access should receive ongoing cybersecurity training to recognize phishing attempts and other social engineering threats.
In December 2024 Atrium Health disclosed a privacy breach impacting nearly 600,000 patients due to online tracking tools embedded in its patient portal from January 2015 to July 2019. These tools, which included tracking pixels from third-party companies like Meta and Google, may have collected and transmitted patient data — such as IP addresses, browsing activity, and personal details from online forms — without consent. Although Atrium Health could not determine if sensitive information was misused, they are treating all affected patients as potentially impacted. According to the report, this was the second data incident the organization reported in 2024, following a phishing attack that exposed information of around 32,000 patients. These incidents underscore ongoing concerns about digital tracking in healthcare, HIPAA compliance, and malicious attempts to access hospital data.
I imply no wrongdoing by Atrium Health, its employees, any contractors and/or its affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a judgement or reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, manipulate, or alter any data I discover. I only take a limited number of screenshots solely for verification purposes and redact those images to protect any potentially sensitive information. I do not conduct any activities beyond identifying potential security vulnerabilities and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.
 The publicly exposed database was not password-protected nor encrypted. It contained 21,344 records with a total size of 6.99 GB. The name of the database indicated that it was an FTP storage repository. In a limited sampling of the exposed documents, I saw .PDF files marked as Billing and Compliance Reports. These contained a detailed account of patient data, such as: Patient PII, insurance coverage details, emergency contacts, anesthesia summary, case summary, diagnosis, case tracking details, names of medical staff, medications administered, patient vital statistics, family medical history, patient medical history, additional notes and summaries by doctors or medical staff.
The PDF documents’ metadata indicated that these were “Software Billing and Compliance Reports” belonging to a medical software company, and contained a detailed analysis and key metrics related to medical billing and healthcare services provided. I immediately contacted that company and provided the details of my discovery. They indicated that they did not own or manage the database and that it was a customer using their electronic health record (EHR) system. Based on the information I provided, this medical software company was able to identify who the documents belonged to and notify that organization. Public access was restricted the same day.
They did not disclose to me who the documents belonged to. However, upon further research, I found a folder marked “Production/Atrium Reports” in the database. The records inside it contained names of medical staff that all appeared to be affiliated with Atrium Health, based on publicly available information .
According to a press release, Advocate Aurora Health and Atrium Health merged in 2022 to create Advocate Health — the third-largest nonprofit, integrated healthcare system in the United States. With its headquarters in Charlotte, North Carolina, the system extends its services across six states: Illinois, Wisconsin, North Carolina, South Carolina, Georgia, and Alabama. The Advocate Health network includes 67 hospitals and more than 500 care locations, and a workforce of an estimated 155,000 professionals, including 10,000 physicians.
I reached out to Atrium Health to inform them that I am an ethical cybersecurity researcher and thus I did not download any sensitive health data, I have no ill intent, and my primary motive is data protection. I received a reply from their cyber incident response team stating: “Thank you for bringing this matter to our attention. We immediately launched an investigation to ensure the issue is resolved. – Advocate Health Cyber Security Team”
It is not known if the database was owned and managed by Atrium Health directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
As a security researcher, the fact that the hospital network has an incident response team and acted quickly to resolve the issue is a good sign and shows a commitment to data security. Furthermore, it should be noted that the medical software company I initially contacted was not involved with the exposure and was very helpful in contributing to secure the publicly accessible records.
Medical compliance documents outline the policies, procedures, and regulations that healthcare providers and organizations must follow to ensure ethical and legal medical billing and coding practices. These documents provide clear billing details, reducing administrative inefficiencies caused by billing or coding errors and providing transparency and accountability. As the documents include personally identifiable health information, they could potentially be subject to regulations such as HIPAA, which mandates stringent security measures.
In this case, each file was labeled as “Billing and Compliance Report” and contained sections that included patient information, anesthesia CSN number, patient class, demographics, anesthesia record ID, active insurance, emergency contact details, case summary, procedure, diagnosis, case tracking events, medications administered, attestation information, vitals, family history, substance use history, post procedure notes, procedure summary, follow up notes, operative notes, and plan of care.
Any data exposure of detailed medical records could potentially pose significant risks. The PII and PHI contained in these records could potentially lead to identity theft, insurance fraud, or social engineering campaigns to obtain additional personal or financial information. Unauthorized access to a patient’s medical history could provide cybercriminals with enough information to attempt a wide range of fraudulent activities. There is no indication that any of Atrium Health’s patient information or health records were at risk of these types of scenarios. The intention is solely to illustrate real-world potential threats based on past cybersecurity incidents within the healthcare sector.
Patient data — such as confidential medical histories, diagnoses, medications, and family health data — is highly valuable on the dark web, making it a prime target for cybercriminals and even nation state actors. Several reports have estimated that a single health record can sell for up to $1,000; for comparison, credit card details sell for about $5, while Social Security numbers are valued at just $1 on the dark web. It is estimated that 97% of threat actors were financially motivated to commit their crimes, so it comes as no surprise that medical providers are one of the biggest targets for cybercriminals.
As such, hospitals and medical providers must take additional security steps to protect their operational data as well as the cloud storage databases where sensitive patient information is stored. One of the easiest ways to do this would be to use strong encryption protocols for both stored and transmitted data. Using encryption can help ensure that patient information remains inaccessible and unreadable even if exposed in a data breach.
In this specific instance, all of the records I saw were in PDF format, readable, and publicly accessible. However, PDF files can easily be password protected, which provides an additional layer of defense in the event of a data exposure. I would also recommend that multi-factor authentication (MFA) be required for all users who have access to cloud storage repositories. MFA, when configured properly, is a great first line of defense for preventing unauthorized login attempts and access. Another good idea is to create role-based access controls (RBAC), limiting access to potentially sensitive records to authorized personnel only.
As a general rule that applies to any industry or service that collects and stores potentially sensitive information, routine security audits and vulnerability assessments should be conducted regularly to identify and patch weaknesses in their systems. I also recommend implementing active monitoring and network detection systems that can help identify unusual or suspicious activity. Real-time monitoring of systems and networks can help identify and respond to potential security incidents before they cause significant harm. Anyone with network access should receive ongoing cybersecurity training to recognize phishing attempts and other social engineering threats.
In December 2024 Atrium Health disclosed a privacy breach impacting nearly 600,000 patients due to online tracking tools embedded in its patient portal from January 2015 to July 2019. These tools, which included tracking pixels from third-party companies like Meta and Google, may have collected and transmitted patient data — such as IP addresses, browsing activity, and personal details from online forms — without consent. Although Atrium Health could not determine if sensitive information was misused, they are treating all affected patients as potentially impacted. According to the report, this was the second data incident the organization reported in 2024, following a phishing attack that exposed information of around 32,000 patients. These incidents underscore ongoing concerns about digital tracking in healthcare, HIPAA compliance, and malicious attempts to access hospital data.
I imply no wrongdoing by Atrium Health, its employees, any contractors and/or its affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a judgement or reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, manipulate, or alter any data I discover. I only take a limited number of screenshots solely for verification purposes and redact those images to protect any potentially sensitive information. I do not conduct any activities beyond identifying potential security vulnerabilities and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected nor encrypted. It contained 21,344 records with a total size of 6.99 GB. The name of the database indicated that it was an FTP storage repository. In a limited sampling of the exposed documents, I saw .PDF files marked as Billing and Compliance Reports. These contained a detailed account of patient data, such as: Patient PII, insurance coverage details, emergency contacts, anesthesia summary, case summary, diagnosis, case tracking details, names of medical staff, medications administered, patient vital statistics, family medical history, patient medical history, additional notes and summaries by doctors or medical staff.
The PDF documents’ metadata indicated that these were “Software Billing and Compliance Reports” belonging to a medical software company, and contained a detailed analysis and key metrics related to medical billing and healthcare services provided. I immediately contacted that company and provided the details of my discovery. They indicated that they did not own or manage the database and that it was a customer using their electronic health record (EHR) system. Based on the information I provided, this medical software company was able to identify who the documents belonged to and notify that organization. Public access was restricted the same day.
They did not disclose to me who the documents belonged to. However, upon further research, I found a folder marked “Production/Atrium Reports” in the database. The records inside it contained names of medical staff that all appeared to be affiliated with Atrium Health, based on publicly available information .
According to a press release, Advocate Aurora Health and Atrium Health merged in 2022 to create Advocate Health — the third-largest nonprofit, integrated healthcare system in the United States. With its headquarters in Charlotte, North Carolina, the system extends its services across six states: Illinois, Wisconsin, North Carolina, South Carolina, Georgia, and Alabama. The Advocate Health network includes 67 hospitals and more than 500 care locations, and a workforce of an estimated 155,000 professionals, including 10,000 physicians.
I reached out to Atrium Health to inform them that I am an ethical cybersecurity researcher and thus I did not download any sensitive health data, I have no ill intent, and my primary motive is data protection. I received a reply from their cyber incident response team stating: “Thank you for bringing this matter to our attention. We immediately launched an investigation to ensure the issue is resolved. – Advocate Health Cyber Security Team”
It is not known if the database was owned and managed by Atrium Health directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
As a security researcher, the fact that the hospital network has an incident response team and acted quickly to resolve the issue is a good sign and shows a commitment to data security. Furthermore, it should be noted that the medical software company I initially contacted was not involved with the exposure and was very helpful in contributing to secure the publicly accessible records.
Medical compliance documents outline the policies, procedures, and regulations that healthcare providers and organizations must follow to ensure ethical and legal medical billing and coding practices. These documents provide clear billing details, reducing administrative inefficiencies caused by billing or coding errors and providing transparency and accountability. As the documents include personally identifiable health information, they could potentially be subject to regulations such as HIPAA, which mandates stringent security measures.
In this case, each file was labeled as “Billing and Compliance Report” and contained sections that included patient information, anesthesia CSN number, patient class, demographics, anesthesia record ID, active insurance, emergency contact details, case summary, procedure, diagnosis, case tracking events, medications administered, attestation information, vitals, family history, substance use history, post procedure notes, procedure summary, follow up notes, operative notes, and plan of care.
Any data exposure of detailed medical records could potentially pose significant risks. The PII and PHI contained in these records could potentially lead to identity theft, insurance fraud, or social engineering campaigns to obtain additional personal or financial information. Unauthorized access to a patient’s medical history could provide cybercriminals with enough information to attempt a wide range of fraudulent activities. There is no indication that any of Atrium Health’s patient information or health records were at risk of these types of scenarios. The intention is solely to illustrate real-world potential threats based on past cybersecurity incidents within the healthcare sector.
Patient data — such as confidential medical histories, diagnoses, medications, and family health data — is highly valuable on the dark web, making it a prime target for cybercriminals and even nation state actors. Several reports have estimated that a single health record can sell for up to $1,000; for comparison, credit card details sell for about $5, while Social Security numbers are valued at just $1 on the dark web. It is estimated that 97% of threat actors were financially motivated to commit their crimes, so it comes as no surprise that medical providers are one of the biggest targets for cybercriminals.
As such, hospitals and medical providers must take additional security steps to protect their operational data as well as the cloud storage databases where sensitive patient information is stored. One of the easiest ways to do this would be to use strong encryption protocols for both stored and transmitted data. Using encryption can help ensure that patient information remains inaccessible and unreadable even if exposed in a data breach.
In this specific instance, all of the records I saw were in PDF format, readable, and publicly accessible. However, PDF files can easily be password protected, which provides an additional layer of defense in the event of a data exposure. I would also recommend that multi-factor authentication (MFA) be required for all users who have access to cloud storage repositories. MFA, when configured properly, is a great first line of defense for preventing unauthorized login attempts and access. Another good idea is to create role-based access controls (RBAC), limiting access to potentially sensitive records to authorized personnel only.
As a general rule that applies to any industry or service that collects and stores potentially sensitive information, routine security audits and vulnerability assessments should be conducted regularly to identify and patch weaknesses in their systems. I also recommend implementing active monitoring and network detection systems that can help identify unusual or suspicious activity. Real-time monitoring of systems and networks can help identify and respond to potential security incidents before they cause significant harm. Anyone with network access should receive ongoing cybersecurity training to recognize phishing attempts and other social engineering threats.
In December 2024 Atrium Health disclosed a privacy breach impacting nearly 600,000 patients due to online tracking tools embedded in its patient portal from January 2015 to July 2019. These tools, which included tracking pixels from third-party companies like Meta and Google, may have collected and transmitted patient data — such as IP addresses, browsing activity, and personal details from online forms — without consent. Although Atrium Health could not determine if sensitive information was misused, they are treating all affected patients as potentially impacted. According to the report, this was the second data incident the organization reported in 2024, following a phishing attack that exposed information of around 32,000 patients. These incidents underscore ongoing concerns about digital tracking in healthcare, HIPAA compliance, and malicious attempts to access hospital data.
I imply no wrongdoing by Atrium Health, its employees, any contractors and/or its affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a judgement or reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, manipulate, or alter any data I discover. I only take a limited number of screenshots solely for verification purposes and redact those images to protect any potentially sensitive information. I do not conduct any activities beyond identifying potential security vulnerabilities and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.