Over 1.2 Million Documents, Including Security Guards and Offenders, Exposed in Data Breach
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to WebsitePlanet about a non-password-protected database that contained over 1.2 million documents belonging to UK-based Amberstone Security Ltd, a technology and physical security services company.
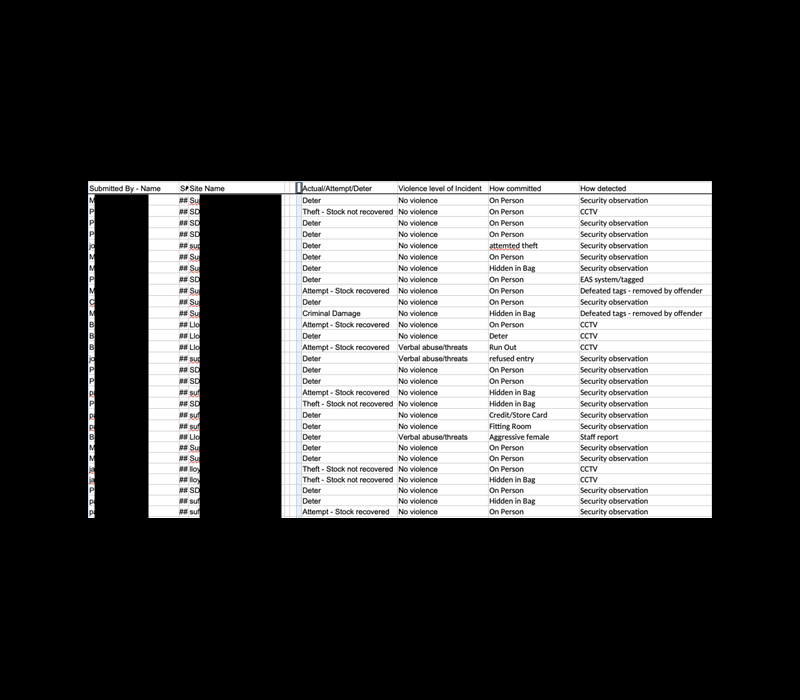
The publicly exposed database contained 1,274,086 documents with a total size of 245.3 GB. These included the PII and images of thousands of security guards, images of security credentials or license cards issued by the Security Industry Authority (SIA), incident reports, as well as names and dates of birth of theft suspects. Upon further research, it was identified that the documents belonged to Amberstone Security Ltd., a UK-based security company that provides security solutions, intelligence-led manned guarding, and loss-prevention services. I immediately sent a responsible disclosure notice to Amberstone Security, and public access to the database was restricted the following day. It is not known how long the data was exposed or if anyone else may have accessed the documents, only a comprehensive internal cyber forensic audit could identify this information.
Amberstone Security restricted public access to the database and replied thanking me for my responsible disclosure notification. “Thank you for bringing this to our attention, this is deeply concerning. I am investigating this with the supplier who developed and hosts the platform. Please rest assured that we take data security seriously, and this will be investigated thoroughly”.
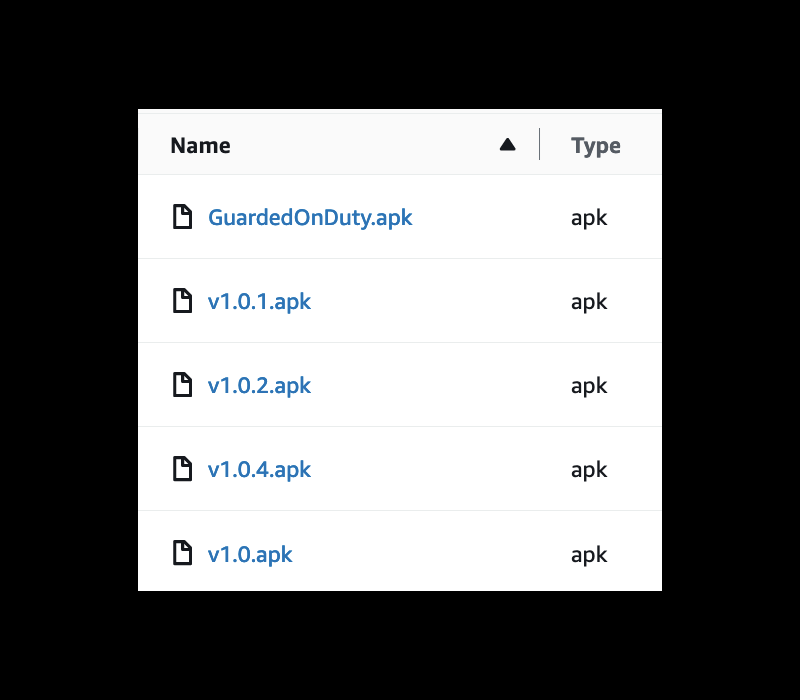
Although the records belonged to Amberstone Security, according to their statement, the database and files were managed by a third-party contractor. I did not receive any additional messages, nor did Amberstone specifically identify the name of the supplier in their response. Amberstone appears to be linked to the Argenbright Group, a privately-held family of companies that provides commercial and government security. It is not clear exactly why these documents were collected and stored. The database also contained development files regarding an application called Guarded On Duty, which was developed by ATWRK LTD. According to both the Google and Apple App Stores, the privacy policy of this application is linked to Amberstone Security. The application lets security guards log in and upload images of their badges and themselves to verify they are working their scheduled shift at a specific job location.
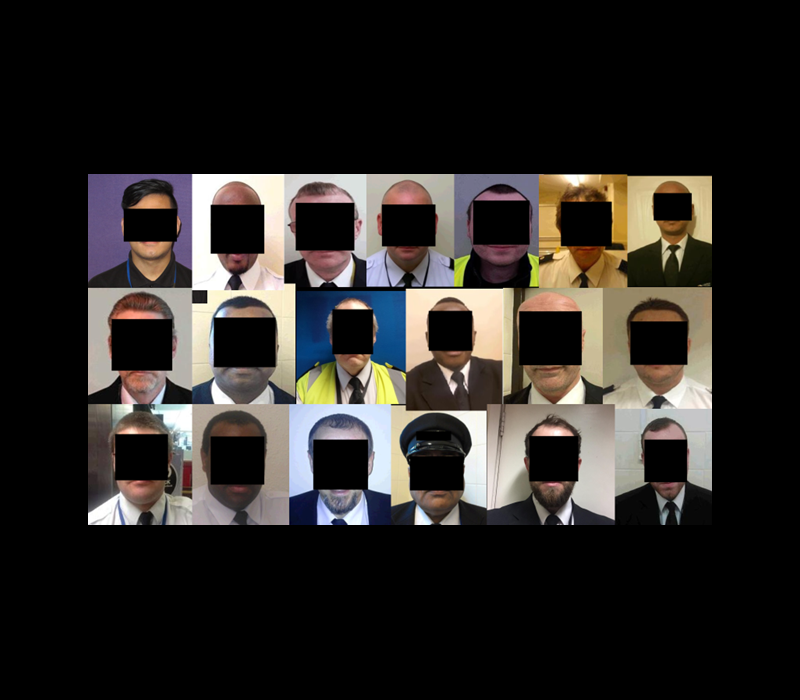
I saw a folder that contained around one hundred thousand images labeled “guard pics”, consisting of: (i) images of security personnel checking in for their shifts using a photograph of themselves and often holding their security badge; and (ii) photographs of guard identification cards. The app store’s summary of security practices indicates the app does not employ encryption and that data isn’t transferred over a secure connection, suggesting that the data is potentially at risk and may be missing some fundamental security safeguards.
The records I saw range from 2017 to 2024. The database also contained an extensive list of customers and businesses that use Amberstone Security’s services. These customers appeared to be from a diverse range of industries including retail, distribution, leisure and NTE, events and hospitality, corporate, finance, healthcare, education, government and criminal justice, agriculture, ports, and residential security.