90% of cyber attacks use a fake email to gain access to your business. Retruster allows employees to know if incoming mail is legit, so they can stay protected from malware, phishing and ransomware that can cost the organization hundreds of thousands of dollars. To get to the bottom of this, I sat down for a video call with Retruster CEO Michael Snape, who explained what phishing emails look like and what can be done to stop them coming in.
Please describe your background and the company’s background. What sparked the idea, and how has it evolved so far?
My story is essentially the story of the company. I was working in the finance department of a large commerce company. We received an email from our CEO to say there was a new opportunity and money needs to be transferred. Of course, it turned out that email was fake. When we looked into it, we realized how easy it was to fake an email. We also realized that this is happening all over the world. There’s no reason to rob a bank and put your life at risk when you can just send a fake email with no consequence whatsoever. It’s super easy and that money disappears immediately so why shouldn’t you do it? It turns out that this problem has only grown as data has become more valuable. As our world has moved more online, this problem has become massive. Furthermore, what started as just small incidences of financial fraud has grown both in terms of the financial scope and the volume of attacks. Emails are the main way of delivering malware, ransomware, data breaches and data exfiltration, accounting for about 98% of cyber attacks. We realized the majority of security issues that organizations are facing can be solved upstream if you secure the email vector. If you can do that, you’re solving so many issues downstream. Unfortunately, email is something that exposes a large part of the organization, because everyone uses it. If I send a phishing attack to the CEO or the CIO, it’s often just as dangerous as sending a phishing attack to the newest intern that started yesterday. For example, we recently started working with a bank. The reason they came to us is that one of the branch staff had opened up an email and had given someone their credentials, and now someone outside of the organization has got full access to their entire internal architecture, and they can move laterally within that system. That’s just a disaster that would have been solved if that bank had Retruster in place. That’s essentially our mission: to secure companies from the number one threat, which is email. The way we decided to do it is very different from the vast majority of current solutions on the market. Most companies use a solution that tries to stop as many emails on the server level as possible before it gets through to the users. That’s only 70% effective, so we are right there next to the user. We will warn them about any email that comes in that looks a little bit suspicious. There’s no question of emails getting through that look fine but are dangerous. A little bit later we’ll talk about why that’s become more of a problem.What kind of threats are people being exposed to via email?
Firstly, there are different types of malware. Once malware gets deployed into your system, often by clicking on a link in an email, the attacker can essentially do whatever they want. They can take data and sell it on the dark web, or shut you down and demand a ransom in exchange for releasing your data. All those things have implications both from a financial aspect, and from a data security aspect, not to mention the regulatory issues, from GDPR to the privacy laws in California, and so on. Can you imagine someone now has all of your passwords and all of your sensitive information? Often, people don’t even know that malware is sitting within one system until days, weeks, and sometimes even years later. The typical example is you get an email that looks like it’s from Netflix, Amazon, or your bank, and it says, please update your account. You put in your account details and then you’re redirected to the real page, but by then, that person already has your details.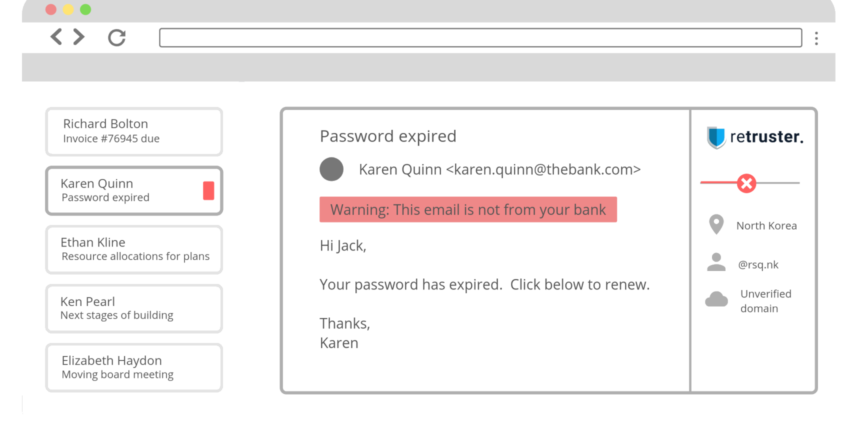 From a business perspective, we see a lot of supply fraud and credential fraud, where a business will get an email saying “our suppliers changed their banking details, please pay into this account”. The next payment goes into that account and obviously, the money disappears.
Almost all cybersecurity threats that organizations face come through the email area, so that’s essentially where that threat lies, even going forward.
From a business perspective, we see a lot of supply fraud and credential fraud, where a business will get an email saying “our suppliers changed their banking details, please pay into this account”. The next payment goes into that account and obviously, the money disappears.
Almost all cybersecurity threats that organizations face come through the email area, so that’s essentially where that threat lies, even going forward.