Inside this Article
| Company name and location: | PLASCHEMA (Plateau State Contributory Health Care Management Agency), based in Nigeria |
| Size (in GB and amount of records/files): | Around 45GB, totaling over 75,000 files |
| Data Storage Format: | AWS S3 bucket |
| Countries Affected: | Nigeria – citizens of Plateau state |

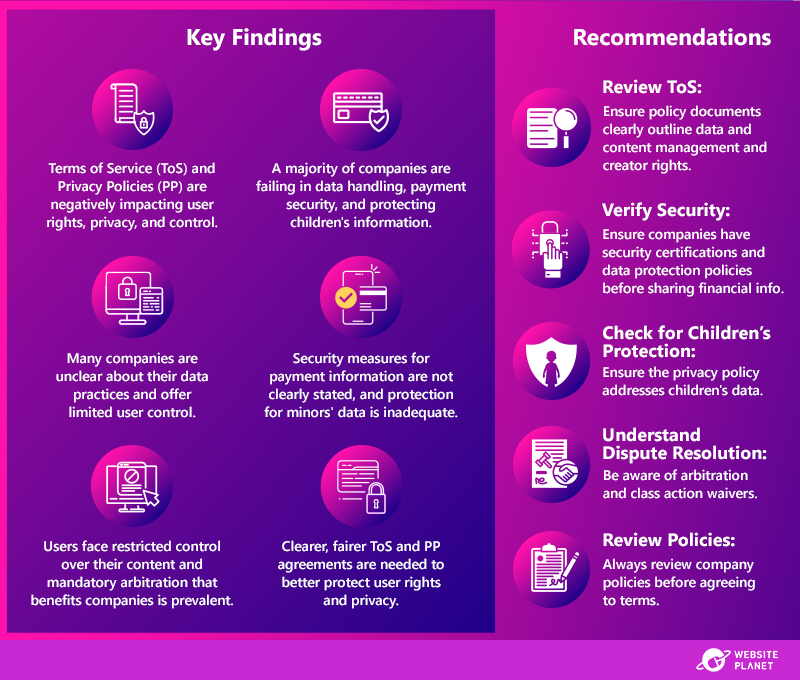
Status of the Data Exposure
We found PLASCHEMA’s open bucket on April 3rd, 2022.- April 5th, 2022: We messaged the Nigerian government.
- April 11th, 2022: We sent follow-up messages to previous contacts and contacted the Nigerian CERT.
- April 14th, 2022: We sent more follow-up messages to previous contacts and the Nigerian CERT.
- April 15th, 2022: We messaged AWS regarding the breach.
- April 25th, 2022: We contacted the Nigerian CERT via Twitter.
- April 26th, 2022 – May 2nd, 2022: We sent several follow-up messages to different Nigerian CERT addresses and received two auto-replies.
- May 10th, 2022: We contacted the Nigerian CERT via Twitter again and they responded, asking for more information.
- May 11th, 2022: We responsibly disclosed the incident to the Nigerian CERT. We also emailed Nigeria’s Data Protection Officer.
- May 12th, 2022: The Nigerian CERT responded to our message, saying “We will ensure the incident is resolved as soon as possible.”
- May 25th, 2022: We contacted the Nigerian CERT again since the buckets were still unsecured.
- May 30th, 2022: The Nigerian CERT responded to our message, saying they suffered a setback while trying to contact PLASCHEMA, but that they had sent a hardcopy letter to the organization.
- Jun 09th, 2022: Contacted the Nigerian CERT again, since the buckets were unsecured. They replied that same day, telling us that they contacted the organization hoping that they would secure the buckets.
- Jul 20th, 2022: All buckets secured.
Customer Data Exposed
- Applicants’ PII: Identity documents containing full names, dates of birth, height, sex, occupation, blood group, address, state, town/village, local government area, place of birth, parents’ full names, registration details, etc.
- Applicant photos: Identification photos of citizens applying to PLASCHEMA’s program.


Impact on Applicants and PLASCHEMA
We do not and cannot know whether malicious actors have accessed PLASCHEMA’s open buckets. However, if hackers have accessed the buckets, they could target citizens with cybercrimes after obtaining their data.- Impersonation: Hackers could impersonate affected applicants online with IDs, PII, and headshots exposed. Many online services accept these documents as proof of identification. Hackers could use this information to join online services in victims’ names and conduct illegal activities and communications.
- Reputational damage: PLASCHEMA’s program is extremely important for Plateau State citizens, especially those from impoverished communities who lack access to proper healthcare. PLASCHEMA’s data exposure could ultimately damage residents’ confidence in the organization’s healthcare program.
Protecting Your Data
Affected Plateau State citizens should monitor social media and other popular sites and services for fake accounts in their names.About PLASCHEMA
Quality healthcare was once a luxury afforded to only the most privileged Nigerian citizens. Now, PLASCHEMA’s program is making professional healthcare accessible to a much broader demographic. PLASCHEMA’s Plateau State Universal Health Care program sets out with the mandate “to ensure access to affordable, equitable, timely and quality healthcare” for Plateau State residents “irrespective of their socioeconomic status.” Citizens apply for the scheme and pay an affordable subscription fee, after which members can purchase medication at a massively reduced cost. We know PLASCHEMA owns the buckets as the organization’s logos regularly appear throughout each bucket’s contents. As listed in the AWS access lists, the same owner operates all 11 buckets.