Inside this Article
Exposed Data
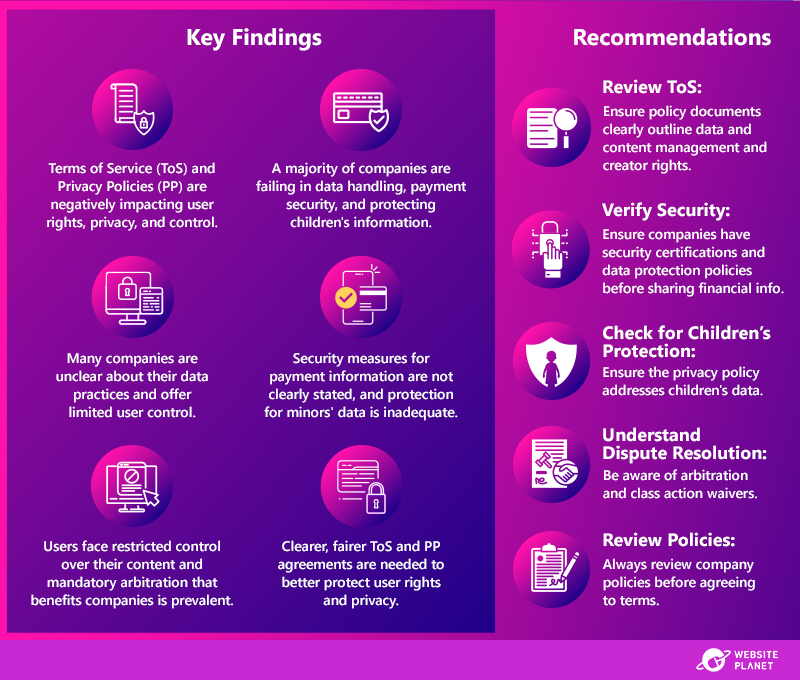
Details related to the company’s shipments, employees, sales representatives and third-party carrier were exposed by the unclaimed bucket, including Personal Identifying Information (PII): Shipment details- Shipment information
- Recipient’s consignee name
- Shipment origin and destination
- Addresses
- Phone numbers (both carrier and recipient)
- Full names
- Phone numbers
- Email addresses
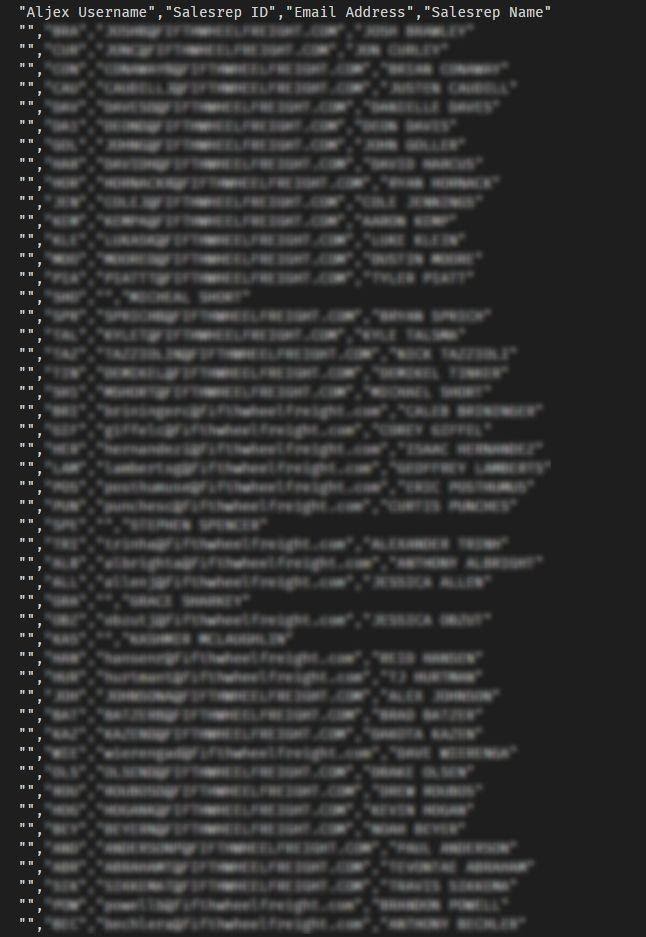
- Aljex Usernames
- Plaintext passwords

- Carrier information
- Full names
- Email Addresses
- Addresses
- Phone numbers
- Passwords
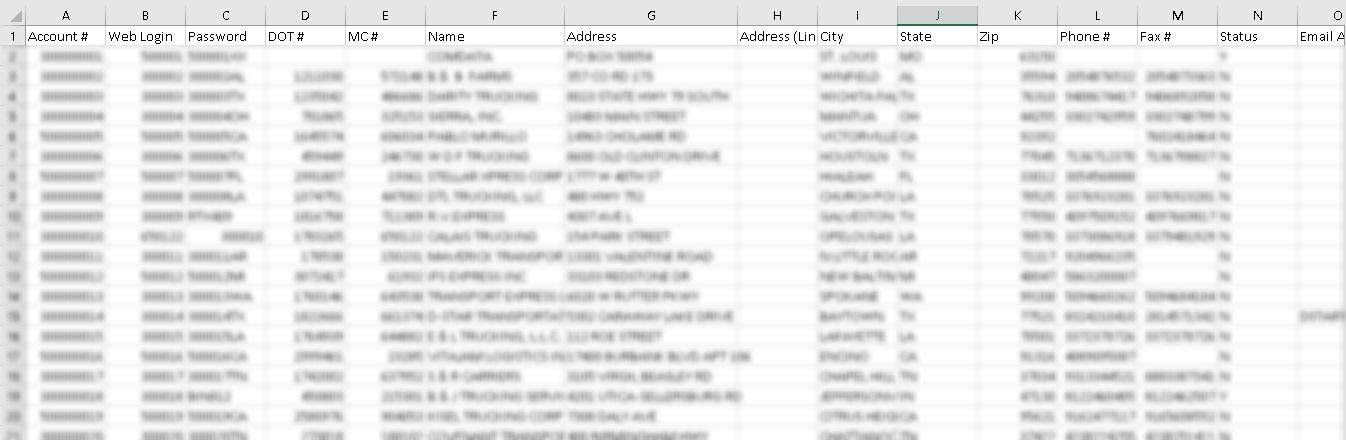
- Full names
- Corporate emails
- Aljex usernames
- Sales representative IDs
Who was affected?
Several groups of people and their data were exposed including employees, sales representatives and third-party carriers.
Whose Data Was Leaked?
The Amazon S3 Bucket was misconfigured and lacked basic security measures and potentially exposed user information to unauthorised third-parties. Anyone with the correct URL could have accessed the Bucket and the files it contained. It’s important to mention that this is due to a bucket misconfiguration on the side of the (unknown) owner, and not due to a problem on the server host.Customer Impact
The likely impact on customers could be severe, given the type of information that was leaked. First and foremost, hackers could leverage the leaked data to assist in fraudulent identification across other platforms. Phishing and malware scams could also be deployed via emails sent to people’s email addresses, including personalised “click-bait” to entice the target into clicking through to an unsecure website. Corporate espionage and anti-competitive practises could occur because of nefarious users migrating or targeting potential clients on the user list. Leaked usernames and passwords is also highly compromising because hackers could hijack the affected accounts and wreak severe damage to the company’s business operations, as well as those of its partners and carriers.Status of the Data Breach
Our research team first detected the breach on 24 December 2020. We contacted Aljex on 30 December 2020 (because the Bucket was named after them and the files included their name) and Amazon Web Services (AWS) on 2 January 2021 to inform them of our findings. We ended up reaching out to Descartes, owner of Aljex, to disclose the leak on February 1st 2021. They got back to us a day after informing us that the bucket wasn’t theirs and that they would “be making efforts to try to identify who this might relate to and let them know they have this open AWS S3 Bucket in their setup”. A few hours later that day the bucket was secured.Protecting Your Data
There was little that the company’s employees, sales reps, customers and carriers could have done to prevent their data from being leaked. The culpability for the server leak lies entirely with the owner of the bucket.How and Why We Report on Data Breaches
Website Planet is an entity that seeks to help its readers stay safe when using any website or online service. However, given that most data breaches are never discovered or reported by the affected companies, conveying current risk information can be problematic. As a result, we seek to identify existing online vulnerabilities that are putting people at risk, to better prepare them for the risks they face online. As an organisation, we follow the principles of ethical hacking and we always work within the remit of the law. We only investigate unsecured and unprotected databases that were discovered at random. We never target specific companies and we always report all our findings to the appropriate authorities, including the affected companies themselves. By reporting these leaks, we help to make the internet safer for everyone.What is Website Planet?
Website Planet serves as the top resource for web designers, digital marketers, developers, and businesses maintaining an online presence. We provide a wide array of useful tools and resources catering to individuals at all skill levels, from beginners to experts. Additionally, we deliver up-to-date reporting on the latest developments in cybersecurity. Our top priorities revolve around honesty and transparency. We have an experienced team of ethical security research experts who uncover and disclose serious data leaks as part of a free service for the online community. This has included a vulnerability in a Romanian real estate portal and a Database containing court records leaking private data. Read about how we tested five popular web hosts to see how easily hackable they are, here.Originally published on March 15th, 2021